MOBILE WORKFORCE MANAGEMENT SOLUTION
MOBILE WORKFORCE MANAGEMENT SOLUTION
BYOD Mobile Workforce Management
Mobile Devices Used In The Work Place
“Nearly 9 out of 10 business users say they use their mobile device to access critical work information.”
It’s called BYOD, or “bring your own device” to work, and it’s the way we operate today. Employees love it, whether they’re using a laptop, smart phone, or tablet to access their email and the corporate network. The upside of this new phenomenon? Employees are more productive and efficient when they can instantly and remotely access information from the field or while traveling. The downside? It’s crucial to safeguard the devices and accessibility, since employees rely on their companies to provide necessary security and liability safety nets. Then, if an employee inadvertently leaves his smartphone in a cab, the company is not subjected to major breaches of security.
“41% of people use their personal mobile device for business purposes without company support.”
–Source: Juniper Networks Trusted Mobility Index
A number of challenges confront businesses managing mobile environments: keeping up with ever-changing technology, leading employees that don’t follow company policies, managing employee expectations, and juggling various mobile devices. Now more than ever, companies need solid solutions.
DP Solutions’ Mobile Business Solutions
Connect and collaborate with confidence
Introducing DP Solutions’ mobile business service, offering custom-crafted workforce mobility solutions that securely connect your people to each other and to the information they need, whether they’re onsite or working remotely. Our cutting edge Mobile Device Management (MDM) monitoring, visibility, and security tools quash threats and risks from mobile devices while upholding your company’s policies and standards.
Threats* to steer clear of:
- Malware – Viruses, Worms, Trojans, Spyware
- Direct attack – Attacking device interfaces, Network DoS, Malicious SMS
- Loss and theft – Risk of unauthorized access to sensitive data, privacy/identity loss
- Data communication interception – Sniffing data as it’s transmitted and received
- Exploitation and misconduct - Online predators, pornography, inappropriate communications, data leakage
*Source: Juniper Networks 2011 Mobile Threats Report, Published February 2012
Our customizable strategy manages your mobility. We’ll ensure that your mobile platform:
- Is safe, accessible, and always available, with secure Wi-Fi access and a secure VPN solution
- Is compatible with existing infrastructure and software
- Has an efficient, intuitive workflow
- Enjoys a strong support plan with full management of the devices and is continually backed up
- Includes devices that can be deployed on a large scale
- Is flexible, and includes devices that employees can select
- Can have its devices remotely locked or wiped in the event of loss or theft
- Adheres to usage policies and procedures
Here’s our method to your success:

Plan: Our mobility experts perform a thorough mobility needs assessment based on your business goals. We create an integration and design strategy, recommend security policies and procedures, and plan for cloud, on-premise, or hybrid delivery.
Build: For a secure mobile foundation, we design the mobile infrastructure, deploy cloud, on-premise, or hybrid hosting, activate a wireless LAN, create unified communications, set up secure access/network security, configure a remote desktop, protect against virus, spam, and malware threats, and implement backup solutions.
Manage: To maintain your mobile security and integrity, we integrate mobile device management (MDM), remotely enroll and configure devices, enforce policy, track devices, perform remote wipes and locking, restore devices, run maintenance, patch, and security updates, provide service desk support, and manage backup solutions. To ensure continuous integrity and optimal performance, we provide ongoing management and support of your mobile network and devices.
The MDM specifics
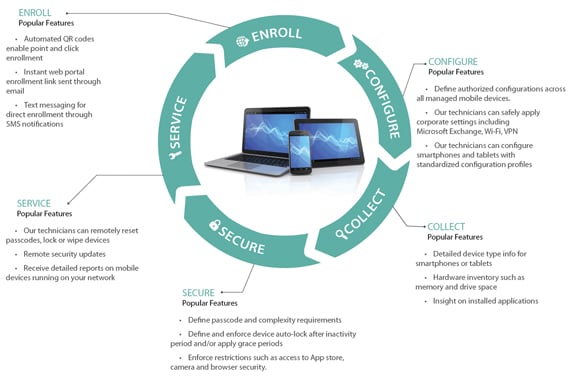
We can easily manage and secure mobile devices throughout their entire lifecycle. Here’s how we do it:
- Enroll allnew and existing employee and company-owned mobile devices rapidly and remotely via SMS text, email, QR code, or URL
- Configure one or more devices instantly to adhere to corporate settings for Exchange, Wi-Fi, VPN, LDAP, and third party email company policies and procedures; configure and enforce corporate policies, including restricting access to explicit media and the use of voice dialing or voice assistant apps
- Collect device information and easily track system inventory
- Secure through intuitive set-up and enforcement of security policies, including passcode complexity requirements, device auto-lock, and the number of failed passcode attempts before a device wipe; instantly lock or wipe mobile devices if a mobile device is lost or stolen; ensure your IT network remains secure from security breaches
- Service by centrally and remotely managing all mobile devices across all of your work sites
Service plans
Complete MDM service plan
Get comprehensive coverage for your MDM at a low monthly, per device fee. We include compilation of all relevant data, device security and services, and implementation of necessary policies and procedures for adequate management and control.
Out of plan security response
If you’re not ready for the Complete MDM Service Plan, you can still take advantage of our mobile device management services. That’s how committed we are to securing and managing any mobile device with access to your network. If a mobile device is lost or stolen, we will attempt to locate the device, recover as much data as possible, and perform a remote wipe of any business and personal information for a one-time fee. Approved remote services will incur a convenience fee in addition to the established hourly service fee.
Contact us to secure your mobile devices today!