The Power of Multi-Factor Authentication

May 20, 2024
In today's hyper-connected digital landscape, where cyber threats are becoming more sophisticated by the day, safeguarding sensitive information has never been more crucial. As businesses and individuals increasingly rely on digital platforms, the need for robust security measures is paramount. One such powerful tool in the cybersecurity arsenal is Multi-Factor Authentication (MFA). In this blog post, we will delve into the key aspects of MFA, exploring its significance, implementation, and the benefits it offers.
Understanding Multi-Factor Authentication
Multi-Factor Authentication lies at the heart of a robust security protocol. It goes beyond the traditional username and password combination by requiring users to provide multiple forms of identification before granting access to a system or application.
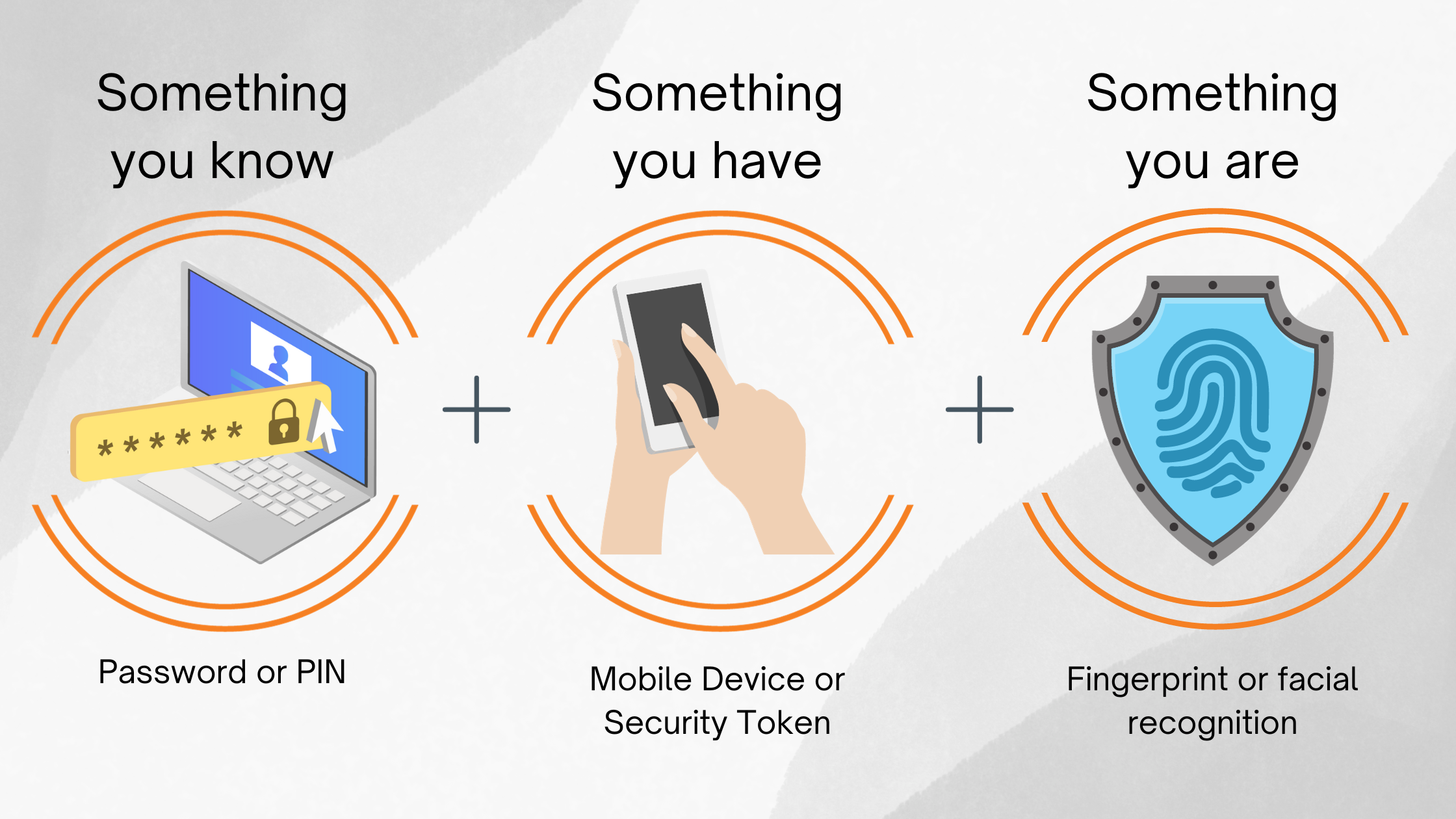
While traditional username and password combinations are susceptible to hacking and unauthorized access, MFA adds an extra layer of security by introducing additional factors. These factors typically fall into three categories:
- Something You Know: This could be a username, password, a PIN or some other form of personal information.
- Something You Have: This involves a physical device, such as a security token, smart card, or a mobile device.
- Something You Are: This refers to biometric data like fingerprints, retina scans, or facial recognition.
The Significance of Multi-Factor Authentication

Multi-Factor Authentication (MFA) is a vital cybersecurity measure that not only enhances security but also helps organizations meet compliance requirements, obtain cyber liability insurance coverage, and deliver a personalized and user-friendly experience.
1. Enhanced Security:Multi-Factor Authentication (MFA) serves as a crucial defense mechanism against unauthorized access by introducing multiple layers of security, thereby significantly enhancing the overall resilience of a system. The primary advantage lies in its ability to mitigate the risks associated with a single point of failure. If one authentication factor is compromised, whether it be a password, token, or biometric identifier, the additional layers of authentication act as formidable barriers that together create a robust defense against malicious intrusions.
2. Compliance Requirements:Many industries are subject to stringent data protection regulations. Implementing MFA not only enhances security but also helps organizations meet a variety of compliance requirements, avoiding legal and financial repercussions. Beyond the direct security benefits, the adoption of MFA can serve as a proactive measure to demonstrate an organization's commitment to data protection and privacy compliance. Many regulations encourage or explicitly mandate the use of strong authentication methods, and implementing MFA positions an organization as being in line with industry best practices. This not only helps in avoiding potential fines and penalties associated with non-compliance but also enhances the organization's reputation by showcasing a commitment to safeguarding customer and employee data.
3. Cyber Liability Insurance:In recent years, many insurance providers have started emphasizing the importance of cybersecurity measures, including MFA, as part of risk mitigation strategies. Insurers are increasingly recognizing that businesses with robust cybersecurity practices, such as the implementation of MFA, are less susceptible to certain types of cyber threats. Consequently, some insurance providers may encourage or even require businesses to implement MFA as a condition for coverage or offer more favorable terms for those with strong cybersecurity measures in place.
4. User Authentication Experience:One of the key strengths of MFA is its versatility in authentication methods. Organizations can deploy a combination of factors, such as passwords, biometrics (fingerprint or facial recognition), smart cards, tokens, or one-time passcodes, to authenticate users. This flexibility enables organizations to accommodate diverse user preferences and needs. Some users may prefer the simplicity of a password and biometric scan, while others might opt for the added security of a hardware token or a mobile app generating one-time passcodes. The ability to choose from these various methods ensures that the authentication process is not one-size-fits-all, allowing organizations to cater to a wide range of user preferences.
Implementing Multi-Factor Authentication

For a successful implementation of Multi-Factor Authentication, it is crucial to follow the 3 steps below:
1. Assessment and Planning
Before implementing MFA, organizations should conduct a thorough risk assessment and identify potential vulnerabilities. A well-thought-out plan ensures a smooth integration without disrupting daily operations.
2. Choosing the Right Authentication Methods:Depending on the organization's needs, different authentication methods can be employed. This could include one-time passcodes sent via SMS, biometric scans, or hardware tokens. The choice should align with the organization's security requirements and user preferences.
3. User Education and Training:
Successful implementation of MFA involves educating users about the importance of security and the new authentication processes. Training programs can empower users to understand the significance of MFA and use it effectively.
The Benefits of Multi-Factor Authentication

There are numerous advantages to implementing Multi-Factor Authentication. Here are three compelling reasons why your organization should embrace this powerful security measure:
1. Mitigating Phishing and Credential Attacks:
MFA acts as a robust defense against phishing attacks, where attackers attempt to trick individuals into revealing their login credentials. Even if the username and password are compromised, the additional factors prevent unauthorized access.
2. Secure Remote Access:With the rise of remote work, securing access to sensitive information from various locations is crucial. MFA provides an extra layer of protection, ensuring that only authorized individuals can access sensitive data remotely.
3. Cost-Effective Security:While the initial implementation may involve some investment, the long-term benefits of MFA far outweigh the costs. The enhanced security and reduced risk of data breaches can save organizations significant financial losses.
Note for Microsoft 365 Users
If your organization uses Microsoft 365, then MFA is already part of your subscription and can be activated by your IT administrator. Once your admin enables it, your users only need to take a few straightforward steps to configure their accounts to begin using it.
Wrapping Up

Multi-Factor Authentication stands as a strong defender against the ever-evolving landscape of cyber threats. As the digital world continues to evolve, embracing MFA is not just a security measure; it's a necessary and proactive step toward safeguarding the integrity of sensitive information. So, strengthen your digital fortress with Multi-Factor Authentication and stay one step ahead in the ongoing battle against cyber threats.
Need help setting up a robust Multi-Factor Authentication solution for your organization?
Additional Resources

 Infographic:
Infographic:
Comments